What Keeps CFO’s Up at Night? – The Cost of Compliance
CFO Regulatory and Compliance Concerns
Chief Executive Officers (CEOs) look to Chief Financial Officers (CFOs) to help keep cost down. According to the Deloitte CFO surveys taken in 2014* CFOs name regulations and the cost of compliance among their uppermost concerns. Regulatory concerns where the most consistently voiced worry during the 2nd quarter of 2014** . If your CFO is concerned, you should be too. CFOs specifically stated concerns about:
- New regulations.
- The lack of clarity around those regulations.
- The complexity of the regulatory environment.
- The costs of compliance with those regulation.
- Unanticipated impacts and unintended consequences of rules and regulation.
And, when it comes to concerns about industry specific regulations, healthcare, technology and financial regulations were causing the greatest distresses.
Best Practices
What’s the solution?
- Know the pain points of the regulations. Know what the regulators are focusing on by “staying in the know” about regulatory activity; and if regulators have issued audit protocols, measure your operations and systems against those protocols.
- Know the best ways to mitigate the risk associated with the regulations to which your company is subject.
- If your internal team cannot clearly see the risk and ways to mitigate, due to lack of regulatory expertise or because they are too close to the potential problem, bring in the consultants for independent reviews and for expert advice.
CFO Cyber-Security Concern
Also among the concerns of CFOs was cyber-security. And, rightfully so. 2014 was the year of massive breaches in the retail, financial, healthcare, technology, and media industries. It was even an eye-opening year for breaches impacting the federal government.
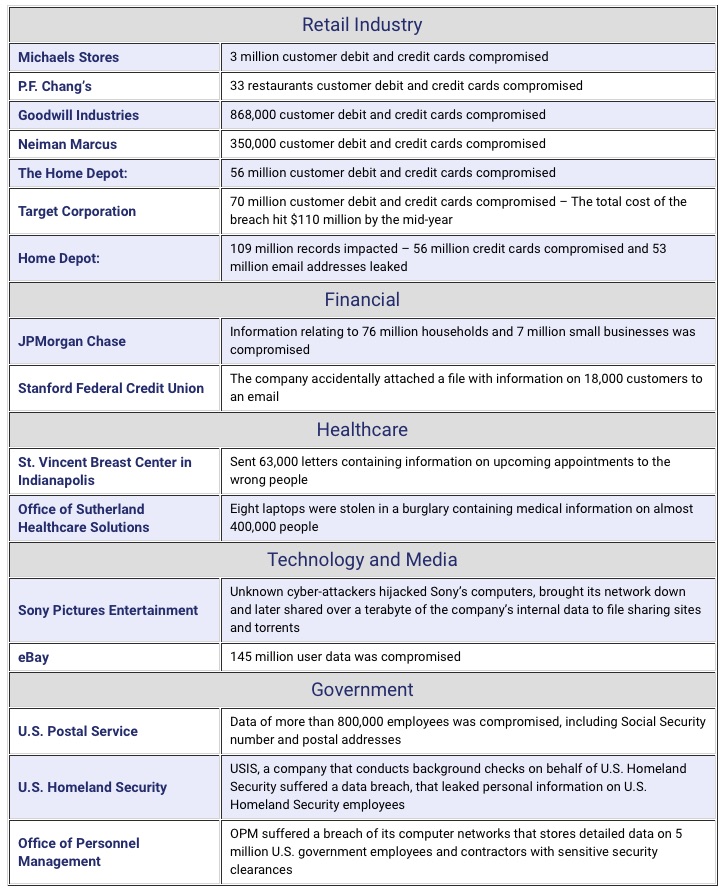
It goes without saying that cyber-security should be a concern. Whether you talking about (1) losses related to system shut-downs or sensitive business data being made public like in the Sony case, or (2) losses connected with reputational damage like some of the retailer cases, or (3) fines and penalties imposed by regulators enforcing HIPAA privacy laws, state security, or state privacy laws – your company has exposure risks.
Best Practices
Section 164.308 of HIPAA provides some good best practices that any business could find useful. Below is my take away from § 164.308:
POLICIES AND PROCEDURES
- Implement policies and procedures to prevent, detect, contain, and correct security violations
- Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports
- Perform a periodic technical and nontechnical evaluation in response to environmental or operational changes affecting the security of electronic protected health information
- Establish (and implement as needed) procedures to restore any loss of data
ASSESSMENTS
Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information.
WORKFORCE AND TRAINING
- Apply appropriate sanctions against workforce members who fail to comply with the security policies and procedures
- Identify the security official who is responsible for the development and implementation of the policies and procedures
- Implement a security awareness and training program for all members of its workforce
SAFEGUARDS
- Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level.
- Implement:
- Periodic security updates
- Procedures for guarding against, detecting, and reporting malicious software
- Procedures for monitoring log-in attempts and reporting discrepancies
- Procedures for creating, changing, and safeguarding passwords
MITIGATE
- Identify and respond to suspected or known security incidents
- Mitigate, to the extent practicable, harmful effects of security incidents that are known to the business
- Document security incidents and their outcomes
*CFO Signals, What North America’s top finance executives are thinking – and doing 4th Quarter 2014 High-Level Report, accessed at http://www2.deloitte.com/content/dam/Deloitte/us/Documents/finance/us-cfo-signals-4q-2014-high-level-report-122314.pdf; CFO Signals, What North America’s top finance executives are thinking – and doing 3rd Quarter 2014 High-Level Report, accessed at http://www2.deloitte.com/content/dam/Deloitte/us/Documents/finance-transformation/us-cfo-signals-3Q14-highlevel-report-092514.pdf; and CFO Signals, What North America’s top finance executives are thinking – and doing 2nd Quarter 2014 High-Level Report, accessed at http://www2.deloitte.com/content/dam/Deloitte/us/Documents/finance-transformation/us-cfo-signals2Q14-report-102214.pdf
** Concerns declined some during the 3rd and 4th quarter.
